Dark Web Explained: Its Impact on Cybersecurity

Source: Image
The dark web, also known as the darknet, is often confused with its counterpart deep web. Thus, to have a clear understanding of the dark web, the two parts of the World Wide Web has to be separated.
Difference between Dark Web and Deep Web
The dark web and deep web are two distinctive things. The deep web can be understood as the entire web that is not accessible by a conventional search engine. The dark web, on the other hand, is a certain website within the deep web that is often associated with criminal activity and illegal market places.
The dark web is only accessible using special software, allowing users and website operators to remain unidentified or untraceable. Though the dark web is often talked about as a hotbed of criminal activity, not everything that happens there is illegal. It has a legitimate side. For instance, users can sign up legally to the social network, BlackBook, described as the “the Facebook of Tor.”
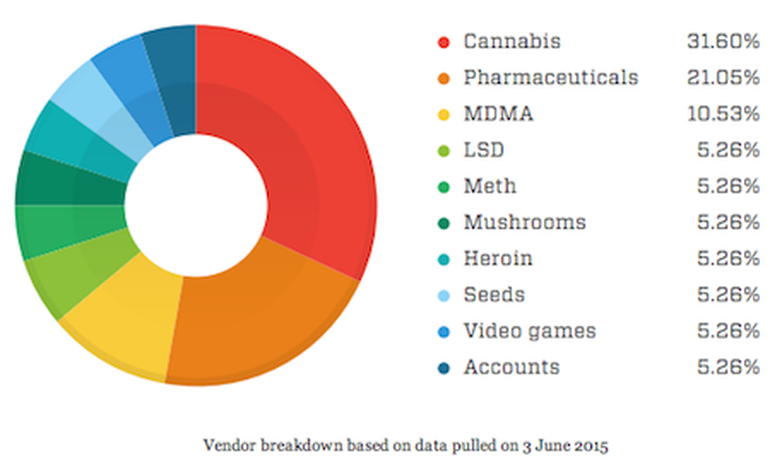
Uses & Access of Dark Web
Uses of the dark web are almost as equally wide and as diverse as the internet. You can use more or less everything, including email and social media, host and share files, and access news websites and do e-commerce.
To access the dark web, you require specific software, configurations, or authorization. Often, you will have to use non-standard communication protocols and ports. At this time, two of the most popular ways to access the dark web are via Tor and I2P.
Tor stands for “onion router” or “onion routing.” It is configured to keep users anonymous.
Basically, you can compare Tor to an onion with multiple layers. Data is stored within multiple layers of encryption and each layer exposes the next relay until the last layer sends the data to its target. Moreover, you can send information in bidirectional ways via the same tunnel. Over two million users are active on the Tor network every day.
Currently, Onion is used by over 2 million users every day and continues to grow exponentially.
I2P, on the other hand, stands for the Invisible Internet Project. It is configured for user-to-user file sharing and collects data and sums it up within multiple layers. The information is grouped with other people’s information so that de-packing and inspection are averted. I2P then sends that data via a unidirectional tunnel.
How to Identify a Dark Web?
The dark web appears like any other site, but there is a difference in structure. While other websites end in .com or .co, dark web sites end in .onion.
Dark web sites also utilize a scrambled naming structure with URLs that can’t be remembered. For instance, a commerce site called Dream Market uses an unintelligible address.
Dark Web’s Impact on Cybersecurity
As per the Global Commission on Internet Governance report, only 0.03 percent of the deep web is available to search engines. And the even-deeper dark web is intentionally hidden and unavailable when using standard browsers. Such a big number of sites unmonitored by internet oversight agencies where all illegal activities take pace pose a risk on cybersecurity.

Let’s take a look at some of the major impacts of the dark web on cybersecurity.
- Ransomware Attacks
As per Cybersecurity Ventures, a new organization will be attacked by ransomware every 14 seconds in 2019, and every 11 seconds by 2021. Ransomware is a type of malicious software configured to block access to a computer system until you pay a sum of money.
The rise in ransomware attacks is linked to the popularity in the use of email services. Cyber Attackers often use email services to carry out their campaigns and remain anonymous.
According to Business Insider, ransomware generates an excess of $25 million in revenue for hackers per year.
- Your Personal Details Could be Stolen
Even if you don’t surf the dark web, you could be at risk of blackmail or even worse if sites you regularly surf are hacked.
As per the Financial Times, over 600,000 individuals’ personal details were stolen from UK companies in 2014. And as cited by The Guardian, stolen credit card details are available only for £1 each on the dark web.
Even ZDNet stated that fake citizenship documents, passports, the services of professional hitmen are out there in the dark web if you know where to look. Malicious people can buy your personal details and use them to blackmail you or other internet users. The Ashley Madison data breach where the group leaked over 25 gigabytes of company data, including user details is an example. The personal information ended up on the dark web for sale.
- Dark Web Hosting Services are Used to Sell DDoS
Cybercriminals and hackers often use dark web hosting services to host websites or e-commerce marketplaces that sell distributed denial-of-service (DDoS) tools and services.
Hackers and criminals can have independent discussions on forums to exchange knowledge, including organizing and coordinating DDoS campaigns and/or exchanging cyberattack best practices.
As per Patrick Tiquet, Director of Security & Architecture at Keeper Security, and the company’s resident expert on the topic, since Tor network has an anonymous nature, it makes it especially vulnerable to distributed denial of service attacks (DDoS).
Usually very unstable hosting services, they can be taken down by the police or vigilante hackers any time for political, ideological, or ethical reasons.
- Malware Infection
Your computer is vulnerable to being infected with malware, software that targets a computer with malicious intent if you visit the dark web without precautions. As per an article in Motherboard, casual visitors to a dark web site can innocently expose their computers to the following programs:
- Vawtrack a program configured to gain access to victims’ financial accounts.
- Skynet used to steal bitcoins or engage in DDoS attacks on other websites with the victim’s computer.
- Nionspy that can capture keystrokes, steal documents, and record audio and video using the infected computer.
Winding Up
For the average internet user, the dark web is a dangerous place. Due to its anonymous nature, it is a breeding ground for illicit activities including the sale of weapons, drugs, fake IDs, and passports.
But at the same time, there are fake websites on the dark web to attract vulnerable victims.
Fake websites are also established by law enforcement to spot and track actual and potential criminal activity.
But since anonymity exists, you can’t identify fake from real. The only way out is to be aware of and use precautions.
—————————————-
About the Author:
Lucy Manole is a creative content writer and strategist at Right Mix Marketing Blog. She specializes in writing about digital marketing, cybersecurity, technology, entrepreneurship and education. When she is not writing or editing, she spends time reading books, cooking and traveling.
Social Links:
Twitter at https://twitter.com/rightmixmktg
LinkedIn https://in.linkedin.com/company/right-mix-marketing
Facebook https://www.facebook.com/RightMixMarketing/
You may also like
-
Find A Solution For Your Sports Field – Tennis Court Lighting
-
Do you need beautifully coded flutter apps? Opt for our cross-form technology
-
You need to consider this before choosing a web design agency for your site
-
Why Substitute Accounting Software With Dynamics 365 Business Central?
-
A Simple Guide on Custom Web Application Development